Safely accept payments online.
Help protect your business when accepting online card and bank payments.
What is an online payment?
Payments made on the internet by credit card or debit card for goods and services are also known as e-commerce or 'card not present' payments. The customer does not need to be physically in store to make the payment. They enter the card details into an online system to complete the transaction.
What are the recommended ways to accept online payments?
Use a gateway hosted page for your website
A payment gateway provider can set up a gateway hosted e-commerce page that integrates with your website. This means when the cardholder makes a payment, they are redirected from your website to a secure payment page hosted by the gateway. The cardholder can then submit their card details on the page and once payment is complete, they are redirected back to your site.
It's important to start working with us early on when you’re setting up your payments page so that we can understand your requirements and make sure you're meeting your Payment Card Industry Data Security Standard (PCI DSS) compliance obligations. Westpac does not permit the use of merchant hosted payment pages.
Westpac supports most major payment gateway providers including:
- Westpac Get Paid
- Verifone
- Worldline
- Windcave
- Mastercard® Payment Gateway Services
- CyberSource
- Datacom
- Paystation.
Use Online EFTPOS to accept payments made by a smartphone
Online EFTPOS is a service provided by Worldline that enables your customers to pay online with their smart phone. Customers enter their mobile number and select their bank on your payments page, then they approve a payment notification within their mobile banking app. Your customers never need to expose their payment or banking credentials.
You can find out more about Online EFTPOS and how to set it up for your business here.
Use batch processing to process multiple online card payments at once
Batch credit or debit card processing is a facility offered by some payment gateway providers that allows you to process multiple credit or debit card payments (a batch) at once. This facility can be used to process different amounts or recurring payments of the same amount.
You can upload a batch of payments directly into a PCI DSS compliant payment gateway provider which removes the need to manually transmit and store volumes of credit card information. Talk to your gateway provider to find out if they offer batch processing and whether you’re eligible for this facility.
Tips to keep your e-commerce payment facility secure.
Take the following steps to help protect your payment facility and reduce the risk of an account data compromise.
|
What to do |
When to do it |
Who is responsible? |
|
Use a 'gateway hosted' solution. |
At set up. |
Merchant/e-commerce solution provider. |
|
Only use PCI DSS compliant third-party service providers. |
At set up. |
Merchant/e-commerce solution provider. |
|
Change default password to system, application and devices. |
At set up. |
Merchant. |
|
Change default admin panel URL. Fraudsters search for websites with default settings because they can be easier to compromise. |
At set up. |
Merchant / e-commerce solution provider. |
|
Create a unique user ID and password for each staff member that has access to your system. |
At set up. |
Merchant.
|
|
Implement multi-factor authentication (MFA). This means users who log into your system must provide at least two pieces of evidence to prove their identity for example by entering their password and an automatically generated code that is sent to their phone. |
At set up. |
Merchant / e-commerce solution provider. |
|
Use HTTPS and the latest SSL security on your website. |
At set up. |
Merchant / e-commerce solution provider. |
|
Install web application firewall. Properly configured firewalls help protect your card data environment by allowing your business to set rules and criteria that restrict incoming and outgoing network traffic. |
At set up. |
Merchant / e-commerce solution provider. |
|
Install anti-virus and intrusion detection tools. The best way to keep anti-virus software up to date is to use a reputable, subscription-based programme. |
At set up. |
Merchant / e-commerce solution provider. |
|
Don't store any card information such as the cardholder PIN or card verification code (three digits on the back of the card). |
Daily. |
Merchant. |
|
Develop a monitoring procedure and action plan. Ensure controls are in place to identify who has accessed the payment gateway portal and create a plan if you detect unauthorised access. |
Regularly. |
Merchant / e-commerce solution provider. |
|
Conduct an external vulnerability scan of your website. |
Quarterly. |
Merchant / e-commerce solution provider. |
|
Ensure your website is patched and upgraded with the latest software, application and security controls*. |
When notified that a patch or upgrade is available or within a month of release. |
Merchant / e-commerce solution provider. |
|
Establish a complex password policy**. If a user has attempted to log in unsuccessfully more than six times, lock their account and reset password after 30 minutes. This will give you time to investigate whether they are an authorised user. |
Passwords should be changed every 90 days. |
Merchant. |
|
Develop an Incident Response Plan |
Annually. |
Merchant. |
|
Monitor your provider's status of compliance. You can check any service provider’s compliance status by asking for their Certificate of Compliance (COC). This will provide the validation date and expiry date of their PCI DSS compliance. |
Annually. |
Merchant. |
|
Conduct staff background check. |
At the start of employment. |
Merchant. |
|
Establish staff security awareness training. |
At the start of employment, and annually thereafter. |
Merchant. |
*Patches are e-commerce platform updates that address security vulnerabilities within a program or product. Software vendors typically release updates to fix performance bugs and provide enhanced security features.
**For example passwords must be seven characters in length and contain a capital and lower-case letter, number and symbol.
Help prevent card fraud.
Stolen or counterfeit cards
Check your online order for these potential red flags:
- Unusual customer details (different delivery details to the card details or the contact person’s name is different from the name on the credit card used for the purchase).
- Larger than usual purchase orders.
- Purchase orders consisting of several of the same items or big-ticket items.
- Orders placed where card numbers used are very similar and/or use sequential card numbers.
- Orders that request rush shipping or overnight delivery.
- Multiple orders shipped to a single address.
- Orders shipped to a country you do not normally deal with.
- Orders shipped to a country where the goods would be readily available in the local market.
- Pressure to deliver goods immediately or unusual delivery instructions.
- A large amount of gift cards or vouchers.
How to help protect against stolen or counterfeit card fraud
- Enable 3D Secure. This is an additional security layer for online credit and debit card transactions. Contact your payment gateway provider to set up 3D Secure.
Refund fraud
Be alert to these requests
- Claims to have overpaid by mistake and requests a partial refund (this is a common card fraud in charities).
- Asks for the amount to be refunded to a different card or payment method such as cash or transfer to a bank account.
- Uses pressure tactics to get the refund quickly.
How to help protect against refund fraud:
- Ensure refunds are processed to the original card used for the transaction.
- Don’t refund money to new cards, Western Union, international money transfers or bank accounts.
- Have a refund policy in place.
- Read our refund fraud article.
BIN attack
- A BIN is the Bank Identification Number – the first six digits of a card. This tells you where the card was issued, in what country and by what bank or financial institution.
- A BIN attack (also referred to as card testing, brute force or an enumeration attack) involves a fraudster taking the first six digits of a card (the BIN) then using software to automatically generate the remaining numbers and test these combinations through online payment channels to see which card numbers are correct and if the cards are active.
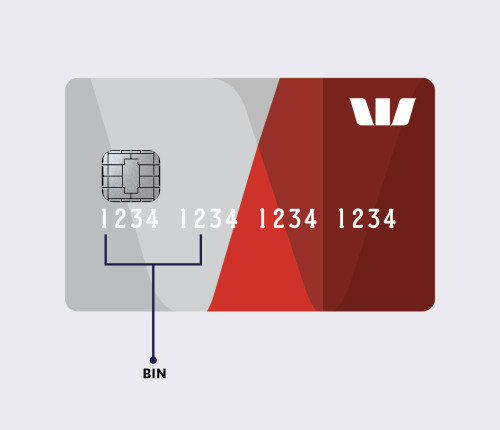
What are the risks of a BIN attack?
- The banks whose cards have been used in the fraud may restrict card payments to your business because of fraud concerns. This could prevent genuine customers from making card payments to you.
- There will be an operational impact – successful transactions will need to be refunded and orders cancelled. Otherwise the rightful cardholders could raise payment disputes (chargebacks) with you and you could be liable for the associated card scheme fines.
- Depending on the nature of the attack, your ability to take card payments may be suspended until fraud prevention measures can be put in place, or even cancelled outright. This could damage your reputation.
Be alert to these signs of a BIN attack:
- Zero dollar or similar small dollar value amounts with high rates of declines. The declines will often outweigh the approved transactions and the volume of these transactions will be high – from ten a day to thousands of cards in the space of a couple of hours. When reviewing the transactions, check the expiry date and security code that is being used. Often fraudsters will use the same or similar expiry dates and security codes.
- Multiple transactions on a single card within 24 hours.
- Unusual cards or locations – think about where your customers are usually located. If you’re suddenly getting orders from all over the world, that should raise a red flag.
How to help prevent BIN attacks
- Enable 3D Secure. This is an additional security layer for online credit and debit card transactions. 3D Secure needs to be set up by your payment gateway provider.
- Enable a CAPTCHA test to tell humans and bots apart. It’s easy for humans to solve, but not bots and other malicious software. Ask your payment gateway provider and web developer how to implement this.
- Set fraud rules for your website. Overseas IP blockers and BIN blockers can prevent transactions from certain countries. You can also restrict the number of payment attempts from a single card within a time frame through your payment facility. Contact your payment gateway and web hosting provider to find out more about these options.
Employee fraud warning signs
Employee fraud
Your business is financially responsible for all card fraud, whether this is carried out by an employee, a cardholder or both in collusion.
Employee refund fraud
- A common type of fraud involves employees issuing refunds to their own account.
- To avoid detection, they may create a large debit transaction on a fraudulent card and refund it to their own card.
- It’s likely to take weeks, even months, before the fraud is detected.
How to protect against employee fraud
- Closely monitor all refunds. Check that all refunds and corresponding debits relate to the same card number. Particular attention should be paid to large refunds.
- Have a separate authoriser of refunds in addition to the person who physically processes a refund.
- Ensure all refunds have appropriate documentation of customer information (name and contact details) and the reason for return or dispute.
- Match refunds to returned or disputed goods or services and verify with the customers that goods or services were returned or disputed.
- Send all refund transactions to a central office for review.
- Fully investigate refunds without matching sales.
General best practice tips to help prevent card fraud
- Reconcile your transactions daily rather than monthly.
- Establish a policy of manager approval or peer review of bank statements to identify suspicious activity.
- Conduct regular internal audits at random times and intervals.
- Audit bookkeeping and accounting processes quarterly.
- Limit employee access to sensitive data and payment systems.
Report suspicious transactions.
If you suspect a suspicious transaction has been made through your merchant facility, contact Merchant Assist.
What's the difference between an account data compromise (ADC) and card fraud?
An ADC is when an unauthorised person gains access to your business environment or payment facility to steal valuable information (like card payment data) with the intention to commit fraud. Card fraud is when stolen card payment data is used to make a fraudulent transaction.
Get in touch.
New customers
Call the Westpac Merchant Services team on 0800 888 066 (option 1), weekdays from 8:30am to 5pm, or email merchant@westpac.co.nz
Existing customers
Contact your Westpac Relationship Manager, or contact our Merchant Services team on 0800 888 066 (option 2), weekdays from 8.30am to 5pm, or email merchant@westpac.co.nz
0800 888 066
- Option 1. New or additional merchant facilities, or to change ownership of an existing facility.
- Option 2. General enquiries on your existing merchant facility including suspicious transactions.
- Option 3. Westpac Get Paid on-the-go or Westpac Get Paid in-store technical support.
- Option 4. Westpac Get Paid online technical support.
- Option 5. Terminal faults that aren't related to Westpac Get Paid.
What’s the best payment solution for my business?
Things you should know.
The information on this page is intended as a guide only. We make no warranty or representation, express or implied, regarding the accuracy of any information, statement or advice contained on this page. We recommend you seek independent advice before acting or relying on any of the information on this page. All opinions, statements and analysis expressed are based on information current at the time of writing from sources which Westpac believes to be authentic and reliable. Westpac issues no invitation to anyone to rely on this material.
Mastercard® is a registered trademark and the circles design is a trademark of Mastercard International Incorporated.
Links to other sites are provided for convenience only and Westpac accepts no responsibility for the availability or content of such websites.
